
Welcome to an ongoing series of articles and deep dives TUNE will be delivering to help marketers find, understand, and take action on fraud. This first article will help build a foundation by introducing the types of fraud marketers face. Let’s get started!
Types of Mobile Advertising Fraud
Fraud can have a tremendous impact on your business. It’s a pervasive issue that cannot be ignored, and it is critical to have the right tools to fight it.
Know your enemy: First things first, let’s cover all the different types of fraud that exist so we can combat it effectively. There are many different ways the ads in your marketing campaigns can be hacked. This blog post will cover some of the most common methods.
To categorize the different types of fraud, we’ll examine two important qualities:
- Characteristics of the ad click: was it genuine?
- Characteristics of the install: was it genuine?
Mobile ad fraud can be grouped into three categories. These categories are:
- Click fraud: fake click, genuine user
- Install fraud: fake click, fake user
- Compliance fraud: genuine click, genuine user
In the table below, red indicates fake and gray indicates genuine.
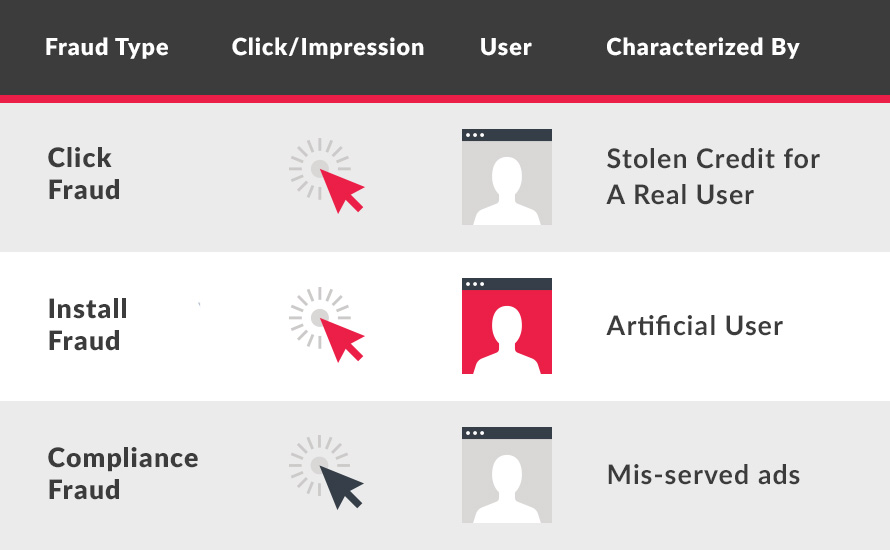
Click Fraud (Identity Theft)
Click fraud occurs when clicks are simulated on a real user’s device even though the ad was not displayed or clicked on. This is a high-return opportunity because it only requires one faked action — the click. Marketers with a large volume of organic users can be especially susceptible.
When the fraudster simulates a click on a genuine user’s device, they take credit once the user installs the app on their own. Since the user is a real human with genuine interest in the app, they behave like the typical organic user and don’t raise a red flag.

Known Crimes
Click stuffing, click spamming
Clicks can be simulated on a mobile device even though the user never clicked the ad. The idea behind this scheme is to maximize chances that the fraudulent partner receives credit when the user ends up installing. Credit might be taken for a user who would have installed the mobile app organically, or stolen from another partner that actually contributed to the install. This tactic is similar to “cookie stuffing” in the old web days.
Non-visible ads
Ad stacking and pixel stuffing are tactics to claim credit for ads that were never actually visible on screen. Ad stacking is when multiple ads are placed on top of each other so only the top ad is visible, and ads on the bottom of the stack are never seen. Pixel stuffing is when an ad is placed in a 1×1 pixel and then packed in a small area. Even though it is not visible, it still registers an impression or click.
Click injection
The Android operating system can broadcast to all existing apps when a new app is installed on a mobile device. Malicious apps take advantage of this broadcast by performing click injection. When the malicious app recognizes a new app being installed, it can run rogue code to fire a click before the new app is opened. Since the fraudster appears to have served the ad that resulted in the last ‘click,’ they get to claim the credit.
Install Fraud (False Impersonation)
Install fraud is a tactic used to impersonate real human behavior when it is actually 100% disingenuous. This form of fraud is designed to quickly scale a user base and drive up costs for the marketer.
These users are not genuinely interested in the app. These are either real humans with malicious intent, or bots that are generating this traffic.

Known Crimes
App install farms
App install farms consist of paid workers who are given mobile devices on which to manually install and uninstall apps repeatedly. These ‘farmers’ can fake in-app purchases to appear as genuine users and stay under the radar. The humans performing these actions have no intention of using the app for its desired purpose. Their only goal is to simulate real traffic to an app.
Bots and botnets
If a mobile device is infected by a bot, it can run code in the background to mimic human behavior. Without the user’s knowledge, bots can install apps and perform in-app activity. Bots can be controlled by a botnet that acts as the master and gives orders. The goal is to deceive marketers into believing these installs are coming from legitimate users.
Compliance Fraud (Misappropriation of Funds)
This type of fraud is characterized by ads served in an environment or context outside the terms the partner has agreed to. This tactic is used to draw in cheaper traffic, while deceiving the marketer into paying a premium price.
This form of fraud draws in real users, but since they were not the ones that should be targeted for the campaign, they may not be the quality or generate the value that the marketer expected to receive.

Known Crimes
Context fraud
This form of fraud occurs when ads are served in the wrong environment or format, or in a place that the marketer has specified against. An example could be ads served on a site that receives a lot of impressions but is not the marketer’s targeted demographic. This is considered compliance fraud since ads are not being served in the right context.
Undisclosed traffic incentivization
Traffic is incentivized when users are offered a reward for performing an action like clicking an ad or installing an app. It may be easier to draw in users when they have an incentive, but there is no guarantee that these users have genuine interest. If a partner is serving incentivized traffic, but the marketer specified that the traffic should not be incentivized, it is a form of compliance fraud.
Mis-targeted ads, geo-masking
The price of traffic can vary based on the location in which it is served. If the marketer’s campaign was to be run in a Tier 1 country to target users with a higher assumed lifetime value (LTV), but instead is served in a Tier 3 country where traffic is cheaper, it is compliance fraud. Usually your Insertion Orders with the ad partner will include geo-targeting requirements. Thus, when users are knowingly targeted outside of these specified locations it is a breach of the contract.
Undisclosed re-brokering
Undisclosed re-brokering occurs when the partner violates their agreement not to sell placements to a third party. When the ad is ultimately shown, it may not reach the audience originally intended, and the marketer may not have transparency into where it ended up being served. Some marketers do not want their campaigns to be re-brokered so they can control their brand and message.
Fraudulent arbitrage
Arbitrage is a necessary component of advertising commerce, and occurs when a partner purchases inventory (often remnant) and resells it at a higher price. Think ‘buy low, sell high.’ In itself, arbitrage is not considered fraud. In many instances, ad networks use arbitrage to effectively increase efficiency and scale. However, it can enable misrepresentation by allowing partners to repackage inventory in a deceptive manner. When lower quality traffic is knowingly substituted, or misrepresented, this can be a form of compliance fraud.
Deceptive ads
This form of fraud involves presentation of an ad in misleading context. It can lead a user to click accidentally, or contain a bait-and-switch where the results don’t meet reasonable expectations. Deceptive ads trick the user into interacting with the ad on a false pretense and are generally created outside of any guidelines you or a reputable marketer would require. If the marketer is going to allow partners to create ads, they can request prior approval to prevent any deceitful activity.
Domain spoofing
During real-time bidding, fraudsters can use domain spoofing to intentionally replace their domain name with a more desirable one with the goal of attracting premium traffic. While the marketer believes their ads are being displayed on one traffic source identified by one domain, their ads are unknowingly being displayed on an unrelated traffic source associated with a different domain.
A Final Word
Now that we have covered the basic types of mobile ad fraud, you will be able to better understand the motives and mechanisms behind each tactic. Knowing the enemy is the first step in combatting ad fraud.
Continue to the next article in the TUNE Fraud Series, Mobile Click Fraud Impact, which dives into click spamming, click stacking, click injection, and beyond.
Author
Becky is the Senior Content Marketing Manager at TUNE. Before TUNE, she led a variety of marketing and communications projects at San Francisco startups. Becky received her bachelor's degree in English from Wake Forest University. After living nearly a decade in San Francisco and Seattle, she has returned to her home of Charleston, SC, where you can find her enjoying the sun and salt water with her family.




[…] A trend we look at is the time difference from click to install. This number can identify two broad classes of click fraud: […]
[…] Welcome to the second installment of the TUNE Fraud Series, articles and insights from TUNE designed to make fraud actionable. Today we do a deep dive on click fraud, characterized by a fake click and a genuine user for a cost-per-install (CPI) campaign. For an introduction to fraud and the series, head over to the first article, Types of advertising fraud. […]