
In today’s digital age, the internet has made it easier for people to connect, share information, and conduct business. However, it has also opened new avenues for scammers and fraudsters to prey on unsuspecting victims.
At TUNE, we take security seriously, and we want to help you stay safe online. Unfortunately, some scammers use legitimate company names and logos to trick people into giving away their personal information. We have noticed one method, called an impersonation scam, popping up more and more over the last few months.
What Is an Impersonation Scam?
One of the most common types of online scams is impersonation scams. In this type of scam, fraudsters pose as legitimate individuals or companies to gain access to sensitive information or money.
One of the most persistent types of deception in this scenario is when a malicious actor acquires a domain that is similar in name to a legitimate website (e.g., g00gle.com). The bad actor then tries to get users to click into the false website without the user realizing they are not on the website they intended to visit. This way, a malicious actor can serve harmful content to the user, such as links to scams or pages that prompt them to enter passwords.
What’s more, the recent rise of artificial intelligence has made it easier to execute these scams. Some bad actors are taking advantage of the breakthrough of generative AI tools such as ChatGPT to create rather convincing fraudulent campaigns. These tools can be used to create more legitimate-looking emails as well as website content. Malicious generative AIs are making their own space in the market, which may prove to be increasingly dangerous, as they’re not limited by the ethical boundaries that are usually defined for their legitimate counterparts.
Main Types of Domain Spoofing in Impersonation Scams
Email Spoofing
With email spoofing scams, attackers send emails that appear to come from a familiar or legitimate sender, such as a friend, business, or government agency. The fraudulent emails may contain a malicious download or link, lure the recipient to a fraudulent website, or redirect the user to a website they did not wish to visit.
Website Spoofing
In this scenario, attackers register a domain that is similar to a legitimate domain. They can then use this domain to create a website that nearly replicates the legitimate site it’s based on and send spoofed emails to lure victims. Once on the spoofed site, users may be offered malicious downloads or asked to provide their personal information, such as login credentials or banking information.
Spoofed websites can also be used to commit advertising fraud. The scammer submits the false domain to an ad exchange in order to trick advertisers into bidding for space on the spoofed site instead of on the legitimate website.
Impersonation Scams: A Case Study
Like many companies that provide their services online, we have faced bad actors with fraudulent websites that attempt to impersonate TUNE.
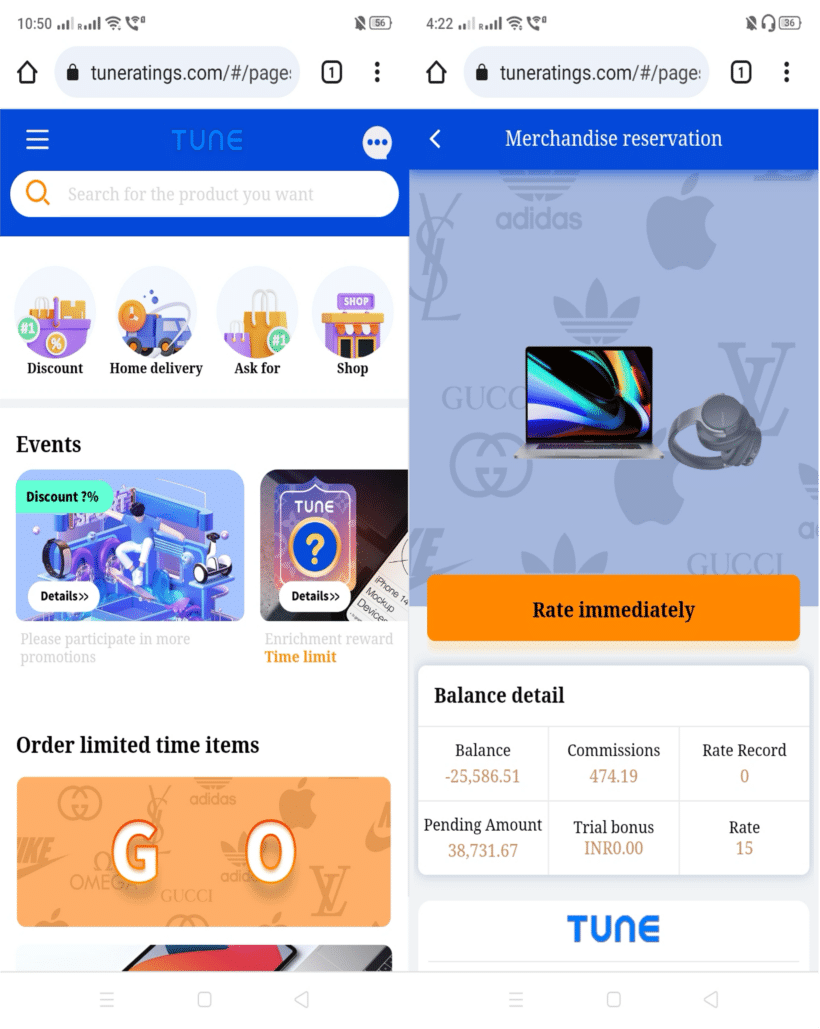
One of these, tuneratings.com, is a website that claims to offer discounts for leaving ratings and reviews of different products; this process includes paying a certain amount to them. This website is not associated with TUNE and should not be trusted or visited for any reason.
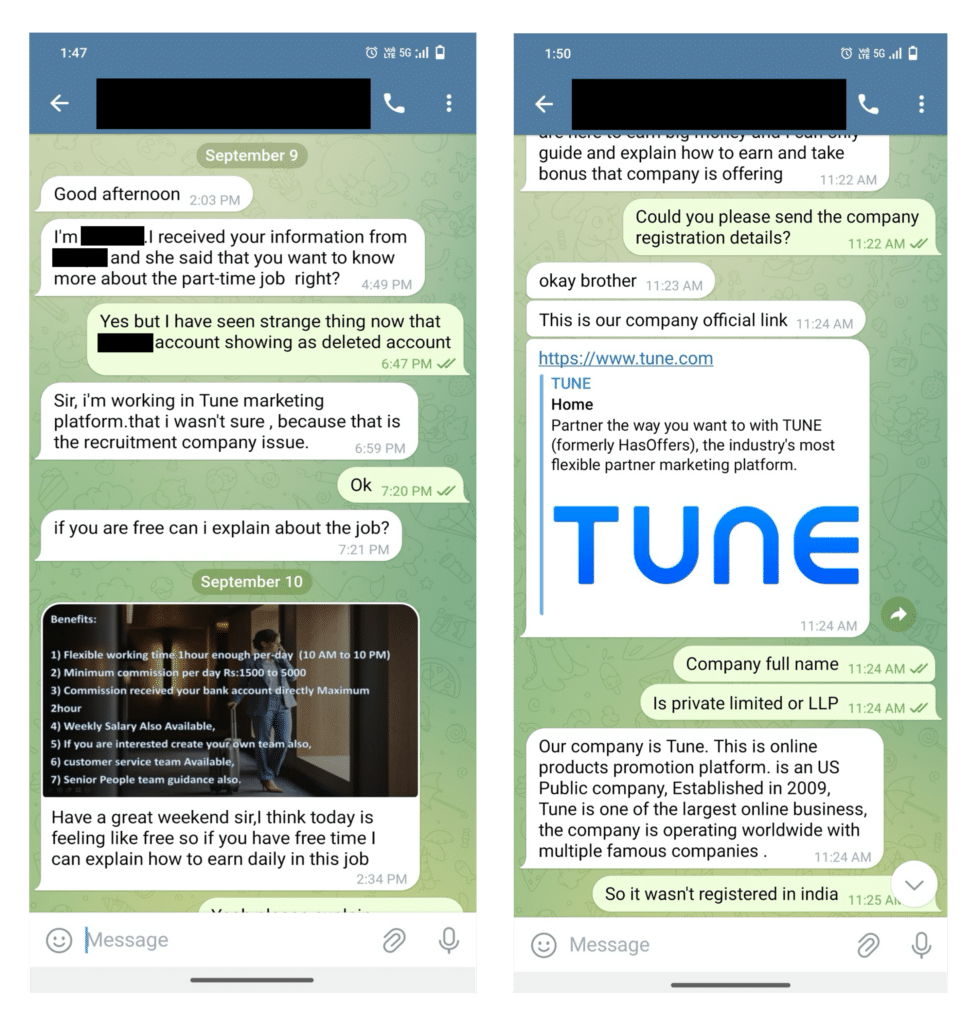
Actors associated with this fraudulent site have recently reached out to customers of TUNE, attempting to have them sign up for unrelated services. Based on reports provided to us, it appears the malicious actors have primarily targeted regions in Southeast Asia. In these cases, the malicious actors tried luring people in by claiming to offer a “part-time job,” and usually used Telegram as their messaging platform of choice.
We’re posting a conversation we had with a potential victim below to spread awareness about this scam and to help others identify and avoid these bad actors:
How to Protect Yourself Against Scams
It’s essential to stay vigilant and take steps to protect yourself against potential bad actors. If you come across this or any other impersonation scam, or even a website or email you think may be a scam, there are a few things you can do. Here are some tips to help you spot and avoid these kinds of scams:
- Be wary of unsolicited emails or messages. Scammers often use phishing emails or social media messages to trick you into clicking on a link or downloading a file. If you don’t recognize the sender, don’t open the message.
- Check the website’s URL. If you receive an email or message from a company asking you to log in to your account, double-check the website’s URL to make sure it’s legitimate. Scammers often create fake websites with similar URLs to trick you into giving away your login information.
- Look for the classic signs of a scam. Scammers often use urgent or threatening language to pressure you into acting quickly. They may also offer rewards or discounts that sound too good to be true.
- Use two-factor authentication. Many online accounts now offer two-factor authentication, which requires you to enter a code sent to your phone or email, use an authentication app, or provide a backup code to log in. This extra layer of security can help prevent scammers from accessing your account.
Remember: If something seems too good to be true, it probably is. Be cautious when sharing personal information online, and always double-check the legitimacy of a website or message before taking any action.
What to Do If You Suspect a Scam
If you are the victim or target of a scam, or spot one in the wild, we encourage you to inform the company being misrepresented through their official channels. Provide all the relevant information you can, and do your best to spread awareness among your circle to look out for the scam and anyone associated with it.
If you suspect any misrepresentation of TUNE circulating around the internet, we ask that you immediately report it to our team by sending an email with all relevant evidence to [email protected]. This will allow our security team to investigate as soon as possible and better protect you and all TUNE customers. Thank you!
Author
Twaha Shah is a Google Certified Cybersecurity professional with a love for offensive security, travel, and football.




Leave a Reply
You must be logged in to post a comment.